Get the Big Picture view of campus safety
CampusOptics is a cross-functional EH&S platform designed specifically for institutions of higher education. CampusOptics was created to help campus safety professionals improve collaboration, reduce institutional risk and enhance safety culture.
An EH&S solution that is as Mobile as you are
EH&S Professionals are almost never at their desks, which is why CampusOptics offers a mobile app for both IOS and Android devices to support on-the-go access to chemical inventory, hazardous waste containers, inspections, safety assets, incident records and emergency plans.
Barcode & QR code scanning
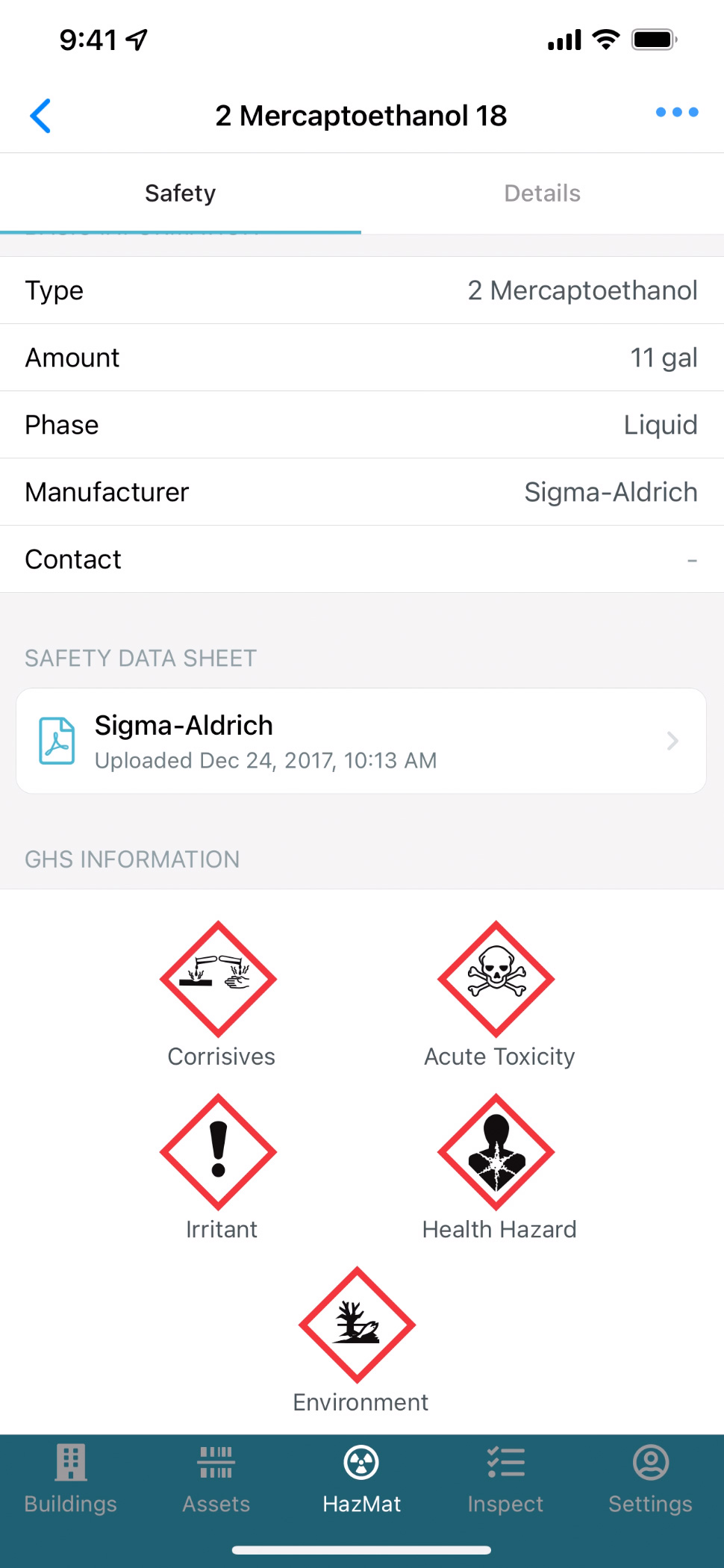
Use your device’s camera to scan bar/QR codes for key information on safety assets or chemical containers.
In-App Photos and Video
Quickly associate pictures and videos to assets, chemical containers, safety issues and inspection reports.

Talk-to-Text
Streamlin
Access Documents
Access key documents on your mobile device, including Safety Data Sheets, emergency plans, floor plans and product documentation.

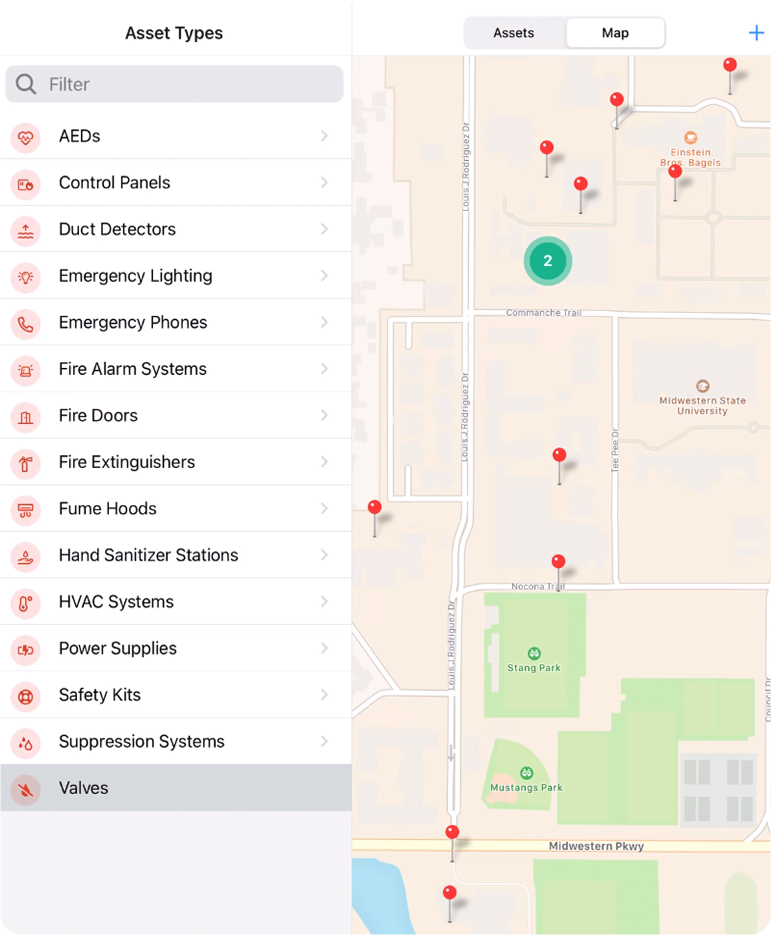
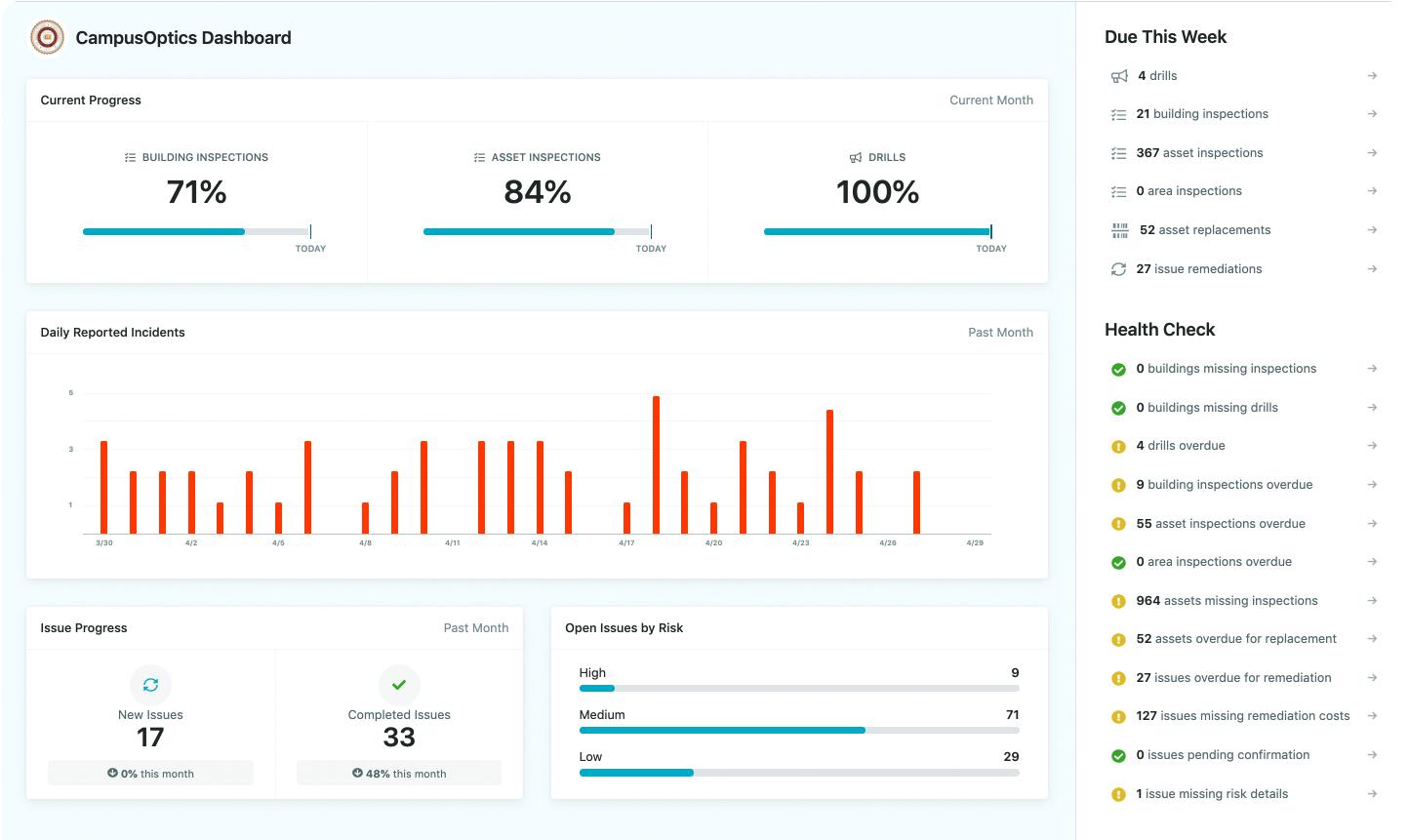
Visualize your data
View the location of safety assets, chemical containers, incidents and safety related issues across campus. Generate public facing maps of key assets like AED’s and Blue Phones.
Locations can be mapped automatically via import or you can log coordinates using your mobile device.
Get the Big Picture view of campus safety
CampusOptics is a cross-functional EH&S platform designed specifically for institutions of higher education. CampusOptics was created to help campus safety professionals improve collaboration, reduce institutional risk and enhance safety culture.
Database security today goes far beyond protecting against unauthorized access — it’s about ensuring compliance, preventing breaches, and safeguarding sensitive data across complex environments. From GDPR and HIPAA to SOX and industry-specific frameworks, organizations must secure their databases while also meeting evolving regulatory requirements.
The best database software for security and compliance provides these capabilities in a unified way, replacing fragmented tools and manual monitoring with centralized protection, real-time analytics, and automated compliance checks. With features like encryption, role-based access controls, vulnerability scanning, auditing, and detailed reporting, teams can prevent data loss, respond quickly to threats, and maintain alignment with global regulations. This approach turns database security from a reactive defense into a proactive strategy for resilience, transparency, and long-term trust.
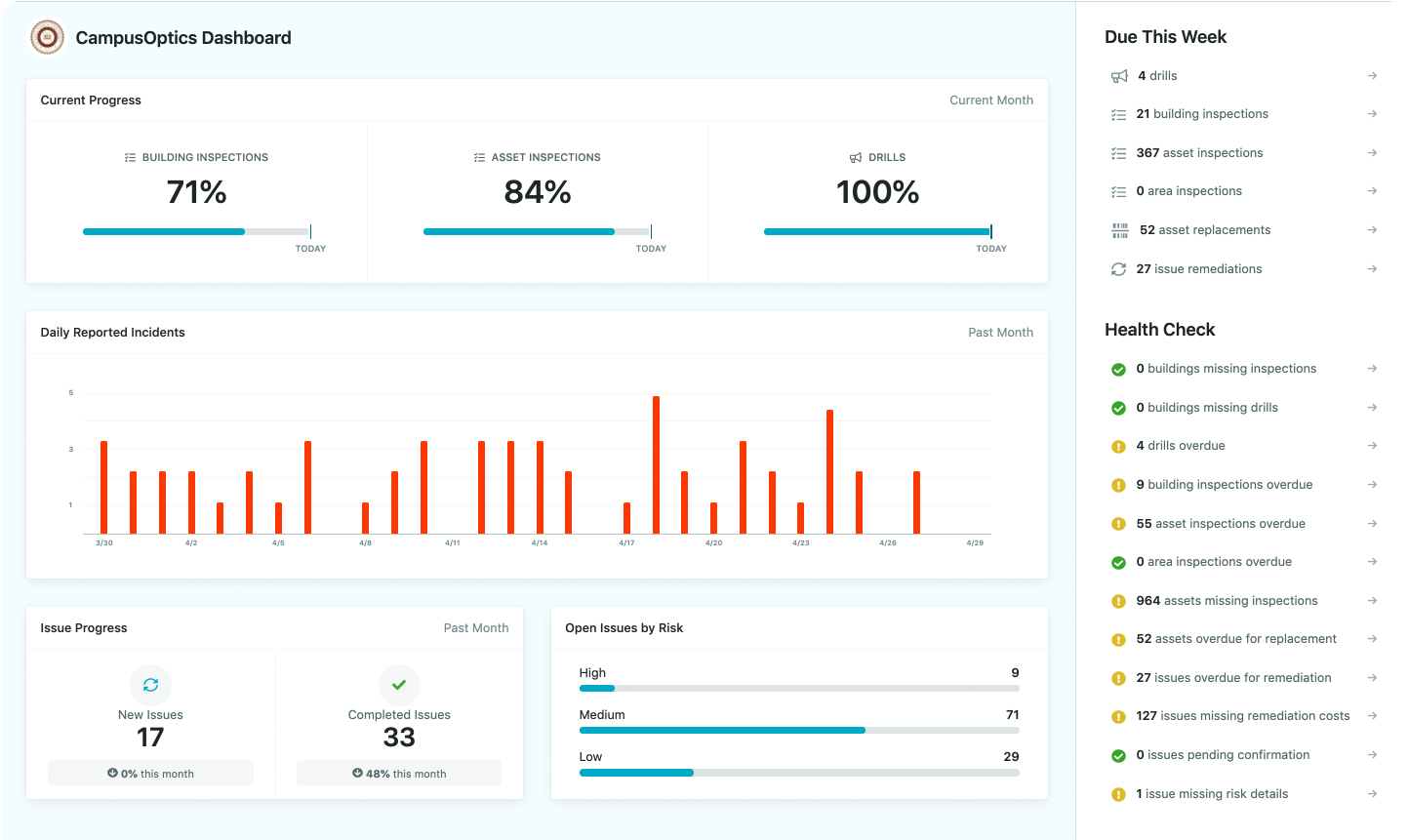
1. CampusOptics
We provide a compliance platform created for higher education institutions that need structured oversight of environmental health, safety, and fire and life safety requirements. We centralize functions such as chemical inventory, hazardous waste tracking, inspections, and radiation oversight, while also including broader features like incident reporting, training assignments, and compliance calendars. The platform was designed after real incidents on university campuses, which shaped the focus on improving access to safety information and streamlining processes for managing compliance.
Although primarily focused on higher education, we handle large volumes of structured compliance data that require the same principles of security, monitoring, and access control found in database compliance platforms. That places CampusOptics within the broader category of compliance software vendors and gives it relevance to discussions of database security and compliance. We offer desktop and mobile access, barcode and QR code scanning, in-app photos and video, talk-to-text entries, and mapping tools to visualize assets and issues across campus environments. These features help institutions maintain accurate records, track risks, and keep compliance information consistent across departments, aligning with the expectations of secure and compliant data systems.
Key Highlights:
- Built specifically for higher education safety and compliance management
- Centralized handling of chemical inventory, waste, inspections, and radiation data
- Mobile functionality with barcode/QR code scanning, photos, video, and talk-to-text
- Mapping tools for safety assets and issues across locations
- Configurable permissions and single sign-on authentication
Services:
- Chemical inventory and safety data sheet management
- Hazardous waste tracking and manifest oversight
- Laboratory, building, and asset inspections with remediation workflows
- Incident logging and investigation management
- Permit creation and approval for high-risk activities
- Occupational safety assessments and training assignments
- Compliance calendars and reporting features
- Emergency pre-plan and floor plan documentation
- Cross-functional access for EHS, risk, fire, and emergency planning teams
Contact Information:
- Website: www.campusoptics.com
- App Store: apps.apple.com/ua/app/campusoptics
- Google Play: play.google.com/store/apps/campusoptics
- Address: 7951 Shoal Creek Blvd., Suite 275 Austin, TX 78757
- Phone Number: (888)748-7652
- Email: contact@campusoptics.com
2. Oracle
Oracle delivers a broad platform that combines cloud applications with cloud infrastructure to support business processes and data security needs. The suite is designed to unify finance, operations, and analytics within a secure environment that can be scaled across industries. With tools for governance and compliance built into its infrastructure, organizations can manage sensitive information while keeping workflows consistent across global operations.
The platform also emphasizes adaptability, providing options for migrating enterprise workloads, running cloud-native applications, and applying AI-driven analytics. Security practices are integrated throughout its services, ranging from identity controls to zero-trust models. This setup makes it suitable for enterprises seeking to consolidate technology systems while maintaining visibility and oversight of compliance requirements.
Key Highlights:
- Combination of cloud applications and infrastructure
- Security practices aligned with compliance frameworks
- Support for zero-trust and sovereign cloud concepts
- AI-driven analytics for decision-making
- Consistent processes across multiple industries
Services:
- Cloud-based enterprise resource planning
- Secure cloud infrastructure for workloads and apps
- Analytics and data intelligence services
- Identity and access management
- Tools for compliance monitoring and governance
Contact Information:
- Website: www.oracle.com
- LinkedIn: www.linkedin.com/company/oracle
- Phone Number: +1.800.633.0738
- Facebook: www.facebook.com/Oracle
- Twitter: x.com/oracle
3. IBM
IBM provides a wide portfolio of enterprise solutions that cover security, identity, automation, hybrid cloud, and AI-driven tools. The platform integrates compliance and governance into its offerings, supporting organizations that need to manage sensitive information while meeting regulatory standards. Its technology is designed to help businesses balance data security with operational efficiency, giving them the ability to adapt to evolving requirements.
The company also offers consulting services, analytics, and industry-focused solutions that reinforce its security products. With its background in research and enterprise systems, IBM combines infrastructure with modern tools such as AI agents and advanced automation. This mix positions the platform as a resource for businesses seeking to strengthen compliance frameworks while modernizing their IT environments.
Key Highlights:
- Security and identity management tools
- Hybrid cloud and automation capabilities
- AI-driven models and analytics integration
- Broad industry coverage with compliance focus
- Consulting and support services
Services:
- Data security and identity solutions
- Hybrid cloud infrastructure
- AI and automation tools
- Compliance and governance frameworks
- Industry-specific consulting and support
Contact Information:
- Website: www.ibm.com
- LinkedIn: www.linkedin.com/company/ibm
- Address: 1 New Orchard Road Armonk, New York 10504-1722 United States
- Phone Number: 1-800-426-4968
- Twitter: x.com/ibm
- Instagram: www.instagram.com/ibm
4. Imperva
Imperva delivers a platform designed to secure data, applications, and APIs across cloud and on-premises environments. It includes protections against DDoS attacks, bot traffic, and malicious activity, while also supporting regulatory compliance such as PCI DSS 4.0. The platform consolidates security functions under one system, allowing organizations to monitor risks and maintain application availability even under external threats.
In addition to threat defense, Imperva provides tools for data governance and audit readiness. Features such as visibility into repositories, insider threat monitoring, and streamlined compliance reporting help organizations handle sensitive information more effectively. By embedding security controls into development and operational processes, the platform supports both protection and long-term compliance.
Key Highlights:
- Application and API protection
- Multi-layered security against DDoS and bot attacks
- Compliance with PCI DSS 4.0 and other standards
- Advanced data governance and audit reporting
- Security embedded into DevOps workflows
Services:
- Web application and API protection
- DDoS mitigation solutions
- Data security and privacy management
- Compliance reporting and audit support
- Insider threat and activity monitoring
Contact Information:
- Website: www.imperva.com
- LinkedIn: www.linkedin.com/company/imperva
- Phone Number: +1 866 926 4678
- Facebook: www.facebook.com/imperva
- Twitter: x.com/imperva
5. Satori
Satori positions itself as a modern data security platform built to support organizations handling large volumes of sensitive information in cloud and AI-driven environments. The system is agentless and works across data stores to provide consistent protection without slowing down performance. It focuses on mitigating risks tied to uncontrolled access, lack of visibility, and compliance gaps, while helping teams stay audit-ready at scale.
The platform offers discovery, monitoring, and access management in a single framework. With features such as real-time activity tracking, just-in-time access controls, and classification of sensitive records, it enables structured oversight of how data is used. By embedding policies directly into workflows, Satori gives organizations the ability to manage compliance and enforce rules in environments where traditional tools often fall short.
Key Highlights:
- Agentless and uniform data security platform
- Discovery and classification of sensitive data
- Real-time database activity monitoring
- Policy-based access controls
- Built for cloud and AI environments
Services:
- Data discovery and classification
- Database activity monitoring
- Data security posture management
- Access management and just-in-time access
- Compliance and audit support
Contact Information:
- Website: satoricyber.com
- LinkedIn: www.linkedin.com/company/satoricyber
- Address: 440 N Wolfe Rd, Sunnyvale,CA 94085, United States
- Facebook: www.facebook.com/SatoriCyber
- Twitter: x.com/SatoriCyber
6. McAfee
McAfee offers a data and identity protection platform designed for individuals and businesses that want to safeguard information across devices and online services. The solution combines threat defense with privacy controls, aiming to prevent scams, malware, and unauthorized access. It also extends into identity and financial protection, providing monitoring and recovery support in the event of fraud.
The system is structured to cover multiple users under one plan, including family members, while maintaining centralized oversight of risks. Features such as secure VPN, personal data cleanup, and continuous breach monitoring allow users to manage exposure in real time. With these tools, McAfee+ serves as an all-in-one package that blends traditional antivirus capabilities with modern compliance and identity-focused security.
Key Highlights:
- Protection against scams, malware, and online threats
- Secure VPN for safe browsing on public Wi-Fi
- Personal data cleanup and privacy management
- Identity and financial monitoring with recovery support
- Multi-user coverage for families
Services:
- Threat detection and antivirus protection
- Scam and deepfake defense
- VPN-based privacy and secure browsing
- Data breach monitoring and personal info cleanup
- Identity theft monitoring and recovery assistance
Contact Information:
- Website: www.mcafee.com
- App Store: apps.apple.com/ua/app/mcafee-security-privacy-vpn
- Google Play: play.google.com/store/apps/wsandroid.suite
- LinkedIn: www.linkedin.com/company/mcafee
- Address: 6220 America Center Drive San Jose, CA 95002 USA
- Facebook: www.facebook.com/McAfee
- Twitter: x.com/McAfee
7. Zscaler
Zscaler provides a cloud-native platform built around zero trust principles, aiming to secure users, workloads, and devices across distributed environments. The system delivers connectivity without relying on traditional VPNs, instead applying identity-based controls that adapt to where and how data is accessed. Its security service edge (SSE) framework includes functions for web and email protection, sandboxing, and data loss prevention.
The platform also integrates advanced analytics and AI-driven monitoring to reduce risks tied to ransomware, lateral movement of threats, and insider activity. With its Zero Trust Exchange, Zscaler connects users directly to applications, minimizing attack surfaces while maintaining fast and reliable performance. This approach is designed to simplify operations and strengthen compliance efforts in complex enterprise networks.
Key Highlights:
- Zero trust architecture with cloud-native design
- SSE platform with TLS/SSL inspection at scale
- Data security and loss prevention capabilities
- AI-driven threat detection and SOC operations support
- Wide ecosystem of integrations with major partners
Services:
- Secure Internet and Private Access (ZIA, ZPA)
- Web, email, and endpoint data loss prevention
- Zero trust firewall and microsegmentation
- Sandbox and browser isolation
- Managed detection, threat hunting, and risk assessment
Contact Information:
- Website: www.zscaler.com
- LinkedIn: www.linkedin.com/company/zscaler
- Address: 120 Holger Way,San Jose, CA 95134
- Phone Number: +1 408 533 0288
- Facebook: www.facebook.com/zscaler
- Twitter: x.com/zscaler
8. HashiCorp Vault
HashiCorp Vault is designed to secure, manage, and control access to secrets, certificates, encryption keys, and sensitive data across distributed systems. Instead of storing static credentials, the platform generates short-lived, just-in-time access tokens that expire automatically, reducing exposure and unauthorized use. This identity-based approach aligns with zero trust practices and helps organizations keep credentials consistent and manageable across environments.
The platform also streamlines compliance and audit preparation by automating secret creation, rotation, and expiration. Vault integrates into workflows with a single API, which allows teams to scale secret management and replace fragmented tools. Beyond protecting secrets, it also inspects repositories for unsecured credentials and connects machines, users, and services with trusted identity verification.
Key Highlights:
- Identity-based access to secrets and credentials
- Short-lived, automatically expiring tokens
- Encryption as a service for data protection
- Centralized lifecycle management of keys, passwords, and certificates
- Integration with zero trust frameworks
Services:
- Secrets storage and access management
- On-demand certificate issuance and rotation
- Encryption for data in transit and at rest
- Automated secret lifecycle policies
- Repository scanning for unsecured credentials
Contact Information:
- Website: www.hashicorp.com
- LinkedIn: www.linkedin.com/company/hashicorp
- Facebook: www.facebook.com/HashiCorp
- Twitter: x.com/hashicorp
9. Thales
Thales provides a portfolio centered on protecting applications, data, identities, and software in cloud and hybrid environments. The platform emphasizes encryption strategies, access management, and application security so organizations can safeguard sensitive information wherever it is stored or used. Offerings are designed to align with compliance needs while maintaining consistent controls across multiple clouds and on-premises systems.
The approach extends to identity and access management for secure sign-in to cloud services and enterprise apps, along with tools that support software licensing and protection. With resources focused on key management, application protection, and governed access, Thales helps standardize security practices for teams operating in dynamic, distributed settings.
Key Highlights:
- Data security with encryption and key management
- Identity and access management for cloud and enterprise apps
- Application and API protection across environments
- Options tailored to cloud, hybrid, and on-premises use
- Guidance and resources aligned to compliance-driven needs
Services:
- Data protection and key management solutions
- Access management and authentication
- Application and API security controls
- Software licensing and protection
- Compliance-focused resources and support
Contact Information:
- Website: cpl.thalesgroup.com
- LinkedIn: www.linkedin.com/company/thalescloudsec
- Address: Arboretum Plaza II 9442 Capital of Texas Highway North Suite 400 Austin, TX 78759 USA
- Twitter: x.com/ThalesCloudSec
- Email: cpl_sales_ams_tg@thalesgroup.com
10. DBmaestro
DBmaestro focuses on database DevSecOps with release automation, source control, observability, and policy enforcement. The platform integrates with CI/CD pipelines to analyze changes, dry-run deployments, and enforce standards before production. The result is controlled, auditable delivery of database updates without adding friction to development.
Compliance and security are addressed through governance features that track changes, prevent drift, and keep approvals consistent. Dashboards and reports support reviews and audits, while automated backout strategies and impact analysis help reduce risk during releases. DBmaestro is positioned for teams that want to align database work with DevOps practices and maintain a clear control plane over change.
Key Highlights:
- End-to-end database CI/CD with policy enforcement
- Source control and drift prevention for database code
- Observability and reporting for audits and reviews
- Dry-run and impact analysis before release
- Integration with existing build and delivery pipelines
Services:
- Database release automation
- Database source control and governance
- Compliance and security policy management
- Observability and metrics for database DevOps
- Backup, backout, and recovery workflows
Contact Information:
- Website: www.dbmaestro.com
- LinkedIn: www.linkedin.com/company/dbmaestro
- Address: 1800 Pembrook Drive Suite 300 Orlando, FL 32810
- Phone Number: 321-607-7229
- Facebook: www.facebook.com/dbmaestro
- Twitter: x.com/DBmaestr
- Email: sales@dbmaestro.com
11. EDB Postgres AI
EDB Postgres AI presents a platform for managing, observing, and operationalizing Postgres for data and AI workloads in public cloud, on-premises, and hybrid environments. The setup focuses on sovereign control, giving teams a consistent way to run transactional databases, analytics, and AI services while retaining governance over deployment choices.
Controls extend to hybrid management, unified observability, and an AI-focused factory that connects enterprise data with agentic use cases. Documentation and a trust center provide visibility into security, privacy, and compliance posture, supporting reviews and due diligence. This configuration suits organizations looking to standardize Postgres operations with predictable controls and clear ownership across environments.
Key Highlights:
- Platform built around Postgres for data and AI
- Hybrid management with unified observability
- Options for public cloud, on-premises, and hybrid
- Emphasis on sovereign operation and governance
- Security and compliance resources via trust center
Services:
- Postgres database platform and tooling
- Hybrid control plane and observability
- AI factory for data-driven applications
- Analytics acceleration options
- Security and compliance documentation access
Contact Information:
- Website: www.enterprisedb.com
- LinkedIn: www.linkedin.com/company/enterprisedb
- Address: 221 W 9th St., Suite 344 Wilmington, DE 19801
- Phone Number: +1(781) 532-6739
- Facebook: www.facebook.com/EDBpostgres
- Twitter: x.com/EDBPostgres
- Email: salesinquiry@enterprisedb.com
12. Varonis
Varonis delivers agentless, cloud-native database activity monitoring with a focus on visibility, threat detection, and automated control. The platform captures queries and maps access to identities, helping teams understand who accessed which data and how. Continuous classification and posture checks support governance across databases, cloud services, and SaaS.
Automation is used to remediate exposures by revoking excessive permissions, masking sensitive fields, and enforcing policies. Unified behavior analytics detect anomalies across the data estate, while identity-centric controls strengthen least-privilege practices. The result is a single layer for monitoring and enforcing database security and compliance at scale without heavy infrastructure.
Key Highlights:
- Agentless, cloud-native database activity monitoring
- Identity-centric mapping of access and permissions
- Data discovery, classification, and posture validation
- Automated remediation for excessive access and exposure
- Behavior analytics for anomalous data use
Services:
- Database activity monitoring and alerting
- Data discovery and classification
- Data security posture management
- Access governance and identity protection
- Policy enforcement and automated remediation
Contact Information:
- Website: www.varonis.com
- LinkedIn: www.linkedin.com/company/varonis
- Address: 801 Brickell Ave.8th Floor Miami, FL 33131
- Phone Number: 1 (877) 292-8767
- Facebook: www.facebook.com/VaronisSystems
- Twitter: x.com/varonis
- Instagram: www.instagram.com/varonislife
- Email: pr@varonis.com
Conclusion
Database security and compliance tools differ in how they approach the challenge, but the overall goal is the same: keeping sensitive information safe while meeting regulatory requirements. Some platforms emphasize encryption and access management, others focus on DevOps integration, monitoring, or automation, but all provide structured ways to reduce risk and simplify oversight.
Choosing the right system often comes down to matching features with the organization’s needs—whether that means handling secrets, ensuring audit readiness, or monitoring activity across hybrid and cloud environments. With clear priorities in mind, these platforms can serve as a foundation for stronger data protection and more consistent compliance.